Introduction
It is essential to protect your company’s IT infrastructure in the modern digital environment. Proactive steps are necessary to guarantee resilience as well as security because cyberattacks such as ransomware, phishing, DDoS attacks, and insider threats are a persistent concern. Let us introduce you to Wazuh, a powerful open-source Security Information and Event Management (SIEM) solution. Imagine a defensive structure where every aspect of your organization is observed, potential breaches are quickly detected, and they are immediately eliminated.
By spreading Wazuh agents throughout your network, you may increase the scope of your monitoring and provide crucial information to your central security operations. Wazuh’s sophisticated threat detection capabilities enable you to quickly respond to threats, whether they are insider threats, DDoS attacks, phishing scams, or ransomware attempts. Wazuh also provides thorough logging and analysis, which enables you to keep improving your defenses by learning from previous instances. The biggest advantage? mental tranquilly. Wazuh is your steadfast defender in a world where cyberattacks are a constant.
Make your organization resilient instead of vulnerable. Wazuh embraces resilience in addition to risk mitigation. To prevent large financial losses, safeguard your environment against dangers including ransomware, DDoS assaults, phishing, and insider threats. Take the necessary actions to enhance your infrastructure security right now. Get in touch with us to guarantee strong protection and a smooth integration of security solutions
Lets discuss some more about it.!
The Importance of a Secure Monitoring Environment
Benefits of Monitoring in an Organization
In today’s digital time, The importance of a strong monitoring environment cannot be overstated. Continuous monitoring and logging are critical components of any organization’s security posture, enabling proactive threat detection and response. By maintaining comprehensive logs of all network activities, organizations can:
- Detect Security Incidents: Identify suspicious behavior in real-time, allowing for immediate investigation and mitigation.
- Ensure Compliance: Meet regulatory requirements by maintaining detailed logs and audit trails.
- Improve Incident Response: Provide context and evidence during incident response, enabling quicker resolution.
- Enhance Visibility: Gain a holistic view of the network, identifying potential weaknesses and ensuring all systems are functioning correctly.
Benefits of a SOC Setup in an Organization
A Security Operations Center (SOC) centralizes an organization’s security operations, bringing together people, processes, and technology to protect against cyber threats. Key benefits include:
- 24/7 Monitoring: Around-the-clock vigilance to ensure continuous protection.
- Streamlined Incident Management: Coordinated response to security incidents, reducing downtime and damage.
- Threat Intelligence: Leverage threat intelligence to stay ahead of emerging threats.
- Centralized Control: Unified view and control over the organization’s security landscape.
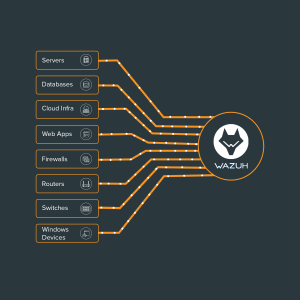
Understanding Wazuh: The Ideal Monitoring Tool
Wazuh is an open-source Security Information and Event Management (SIEM) solution that offers comprehensive monitoring, threat detection, and compliance management. It provides an array of features designed to secure an organization’s IT infrastructure.
Key Features of Wazuh
-
Intrusion Detection
Wazuh analyzes log data to detect anomalies and potential threats. It uses a combination of signature-based and anomaly-based detection methods to identify suspicious activities. This helps in early detection of malicious actions, preventing potential breaches.
-
Compliance Management
Wazuh helps organizations adhere to regulatory standards such as GDPR, HIPAA, and PCI DSS. It provides tools for auditing and reporting, ensuring that all compliance requirements are met. This feature is particularly useful for organizations in highly regulated industries.
-
Vulnerability Detection
Wazuh scans systems for vulnerabilities and provides actionable insights. It integrates with vulnerability databases to keep track of known vulnerabilities and advises on remediation steps. This proactive approach helps in maintaining a secure environment by addressing vulnerabilities before they can be exploited.
-
File Integrity Monitoring
Wazuh tracks changes to critical files, ensuring the integrity of sensitive data. Any unauthorized changes are detected and alerted, enabling immediate response to potential data breaches. This feature is crucial for maintaining the security and integrity of critical system files.
-
Configuration Assessment
Wazuh evaluates system configurations against security best practices. It identifies misconfigurations that could lead to security vulnerabilities and provides recommendations for securing system configurations. This helps in maintaining a hardened security posture across the organization’s IT infrastructure.
Monitoring your Endpoints with Wazuh
One of Wazuh’s strengths is its ability to integrate with various endpoints within an organization’s network. These integrations ensure comprehensive monitoring and logging across the entire IT infrastructure. Here are some key types of endpoints that can be integrated with Wazuh:
Servers
-
Linux/Unix Servers
Wazuh can monitor and log activities on Linux and Unix servers, providing insights into user activities, system changes, and potential security breaches. It supports a wide range of Linux distributions, ensuring compatibility with various server environments.
-
Windows Servers
Integration with Windows servers allows Wazuh to collect logs from the Event Viewer, track system events, and detect unusual behavior. This helps in identifying potential security incidents on Windows-based systems and ensures comprehensive monitoring.
Workstations
-
Windows Workstations
Wazuh can monitor user activities, software installations, and system changes on Windows workstations. This ensures that any suspicious activities on end-user devices are detected and addressed promptly.
-
MacOS Workstations
MacOS endpoints can also be integrated to track system events and user activities. Wazuh provides comprehensive monitoring for MacOS devices, ensuring that all endpoints are secured.
Network Devices
-
Firewalls
Logs from firewalls can be collected and analyzed to detect unauthorized access attempts and potential threats. Monitoring firewall logs helps in identifying and mitigating external attacks targeting the organization’s network.
-
Routers and Switches
Monitoring traffic patterns and configuration changes on routers and switches helps identify network anomalies. Wazuh provides insights into network activities, enabling proactive detection of potential security issues.
Applications and Databases
-
Web Applications
Wazuh can monitor web application logs for signs of attacks such as SQL injection and cross-site scripting. This helps in identifying and mitigating web-based attacks that target the organization’s applications.
-
Databases
Integration with databases enables monitoring of database activities, ensuring data integrity and detecting suspicious queries. Wazuh supports various database platforms, providing comprehensive monitoring of database operations.
Cloud Services
-
AWS
Wazuh can collect and analyze logs from AWS services such as CloudTrail, ensuring compliance and security in the cloud. This helps in maintaining a secure cloud environment and detecting potential security issues.
-
Azure
Logs from Azure services can be integrated to monitor and secure cloud infrastructure. Wazuh provides insights into Azure activities, ensuring that all cloud operations are secure and compliant.
-
Google Cloud
Wazuh supports integration with Google Cloud, providing visibility into cloud activities and security events. This helps in maintaining a secure Google Cloud environment and detecting potential threats.
Monitoring and Alerting
-
Set Up Alerts
Configure alerting mechanisms to notify the SOC team of potential threats. Alerts can be sent via email, Slack, or integrated with ticketing systems. Ensure that the alerting system is properly configured to provide timely notifications of security incidents.
-
Continuous Monitoring
Ensure continuous monitoring by regularly updating detection rules and threat intelligence feeds. Regularly review and update the monitoring configuration to ensure that it remains effective and relevant to the current threat landscape.
-
Generate Reports
Use Wazuh’s reporting capabilities to generate compliance reports for audits. Reports can be customized to meet specific regulatory requirements. Ensure that the reporting system is properly configured to provide accurate and comprehensive compliance reports.
Conclusion
Keeping an environment that is secure for monitoring is crucial for organizational integrity in the modern world. Wazuh is a complete solution that is skilled at logging, keeping an eye on, and strengthening IT infrastructure. Wazuh enables proactive threat management with its rigorous analysis, customizable detection algorithms, and easy integration.
Choosing Wazuh ensures compliance with regulations while also enhancing security. If you are considering implementing Wazuh, our knowledgeable professionals are here to assist you. Effective organization security is our first priority, starting with the initial setup and continuing with ongoing assistance.
Are you prepared to take the first steps towards a safe IT environment? Join together with us to fully use Wazuh’s potential and protect your company from ever-changing risks. Get in touch with us right now to see how we can help you even more.
